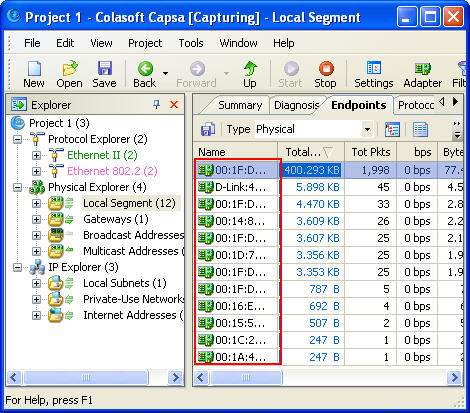
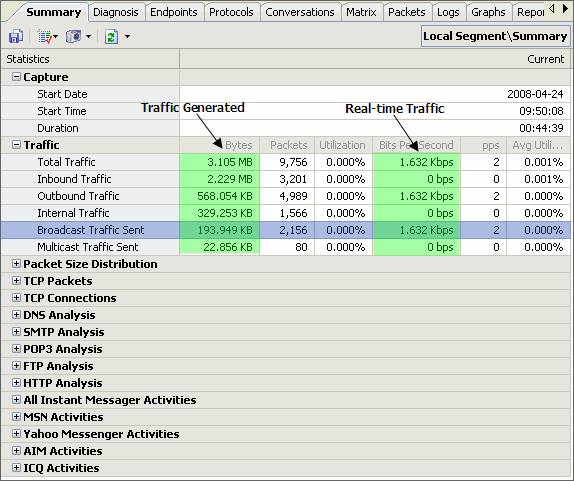
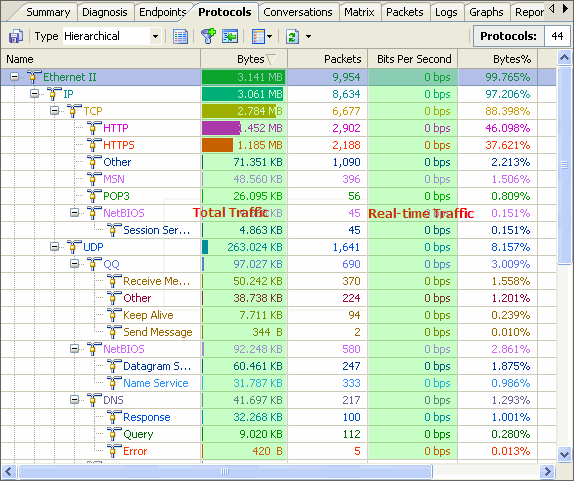
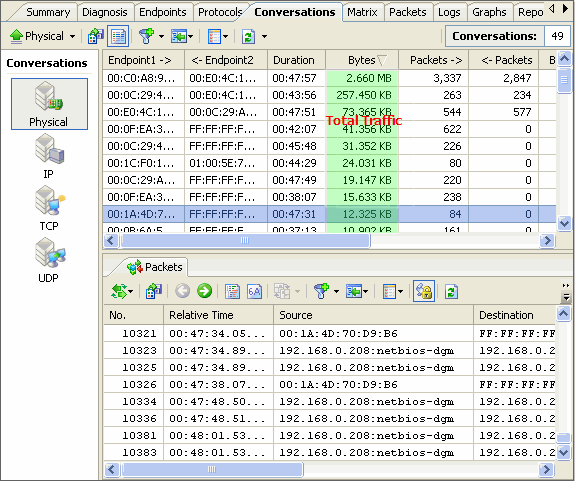
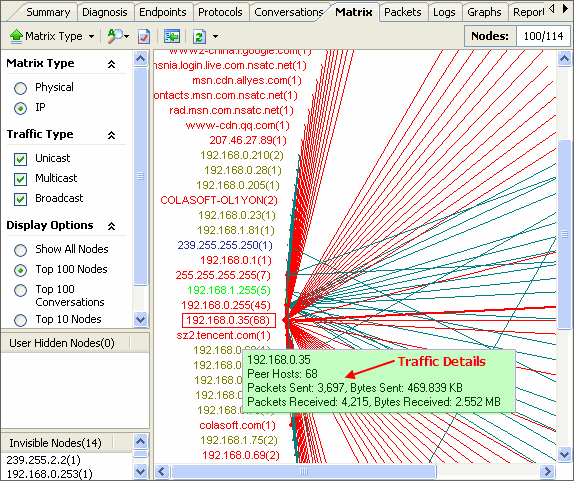
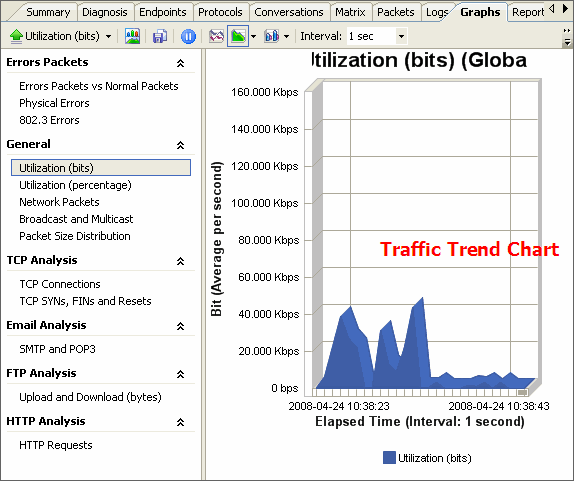
No matter whether you are network administrators or IT managers, you should not be unfamiliar to the network analysis tool - packet sniffer, also known as a network analyzer, protocol analyzer or sniffer) which has been widely used by kinds of organizations, schools, enterprises, government institutions etc.
No matter whether you are network administrators or IT managers, you should not be unfamiliar to the network analysis tool - packet sniffer, also known as a network analyzer, protocol analyzer or sniffer) which has been widely used by kinds of organizations, schools, enterprises, government institutions etc.Maybe you are yet supirsed at why more and more enterprises, like IBM, Intel, Epson, Airbus, Ericsson etc, love to deploy packet sniffer to their company's network? OK, take a fresh coffee now, then look at the following problems, and ask yourself, as a network administrator or IT manager, if these issues are just what you have met?
Rushing from one network problem to another every day?Have no way to judge if your network has been intruded?
Helpless collecting convincing information to submit your boss even if you have realized that your network system has been intruded.
No idea if current network usage is equal to actual need?
Know nothing of how many staffs are not killing their time by chatting with friends, browsing irrelevant webpage etc, but focusing on their job?
Yes, every question listed above has puzzled many network administrators, but no worry, packet sniffer can easily help you out with its strong functions, here are ten reasons make packet sniffers an essential network tools.
* Analyze network problems
* Detect network intrusion attempts
* Gain information for effecting a network intrusion
* Monitor network usage
* Gather and report network statistics
* Filter suspect content from network traffic
* Spy on other network users and collect sensitive information such as passwords (depending on any content encryption methods which may be in use)
* Reverse engineer proprietary protocols used over the network
* Debug client/server communications
* Debug network protocol implementations
Currently, there are dozens of packet sniffers in the market, some are very complex to use like wireshark, you must be versed in networking,; some are designed for common network administrators, such as Colasoft Network Analyzer, all-in-one & easy-to-use, which are more and more accepted and welcome.