The Challenge
As the business is becoming more and more networked, it’s always necessary for network administrators to troubleshoot network issues in shortest time possible if the network is not functioning properly. Network downtime or network malfunction may cause headaching inconvenience or even millions of business losses if not settled up in time. Without a handy tool, network troubleshooting can be time-consuming and frustrating.Old Ways – Time-consuming and Frustrating
There are a lot of articles providing guidance on how to troubleshoot network issues in general ways. For simple networking issues, these tutorials work fine. However, for a company-level network, issues are often complicated and mixed, and these issues require deeper analysis and stronger diagnosis abilities. Obviously, old ways are no longer suitable for today’s in-time network troubleshooting demands.
Troubleshooting Network Issues in Seconds
To troubleshoot your network in time, even in seconds is now possible with Capsa’s diagnosis feature. Network issues are automatically detected and clearly identified, with possible causes and solutions provided.
Automatic Diagnosis
Based on Colasoft’s packet analysis engine, Capsa is able to automatically detect network issues in different OSI layers, such as application layer, transport layer, and network layer. All these issues are marked with different severity levels, indicating which are critical issues that need to be addressed immediately, which are just informative messages.

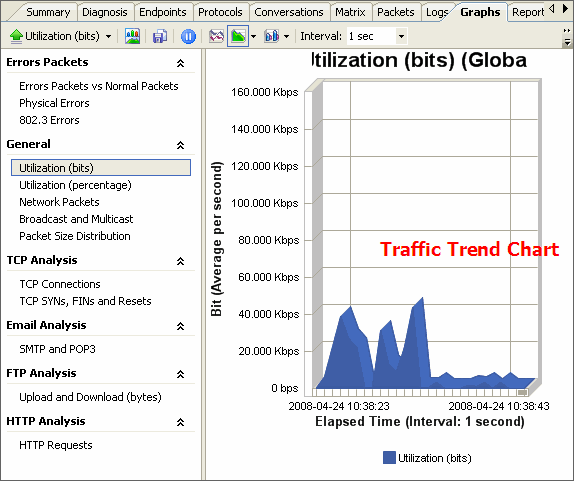
(Figure 1 Diagnosis Events List)
Quick Locate Suspicious Host
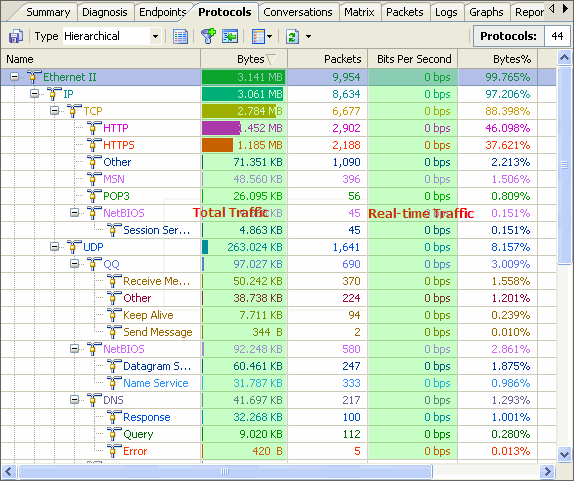
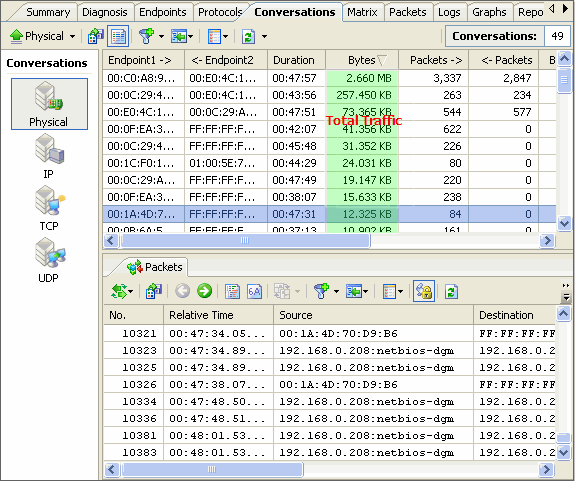
Once a critical network issue is detected and requires immediate handling, we can select the item from the list, then detailed information will be provided under, including source, destination, port and so on. We can easily locate the suspicious host in this field, for example, the attacking host or the host which is spamming our network. Moreover, after locating the suspicious host, we can conduct deeper analysis, such as protocol analyzing or packet decoding.

(Figure 2 Diagnosis Details)
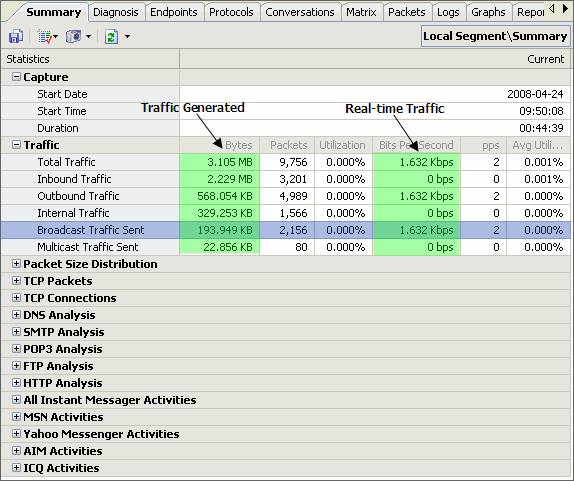
Possible Causes & SolutionsWhen selecting a network issue from the list, possible causes and solutions are also provided for users to understand the issue and solve it as soon as possible.

(Figure 3 Possible Causes & Solutions)
CustomizableDepending on network sizes and network’s characteristics, we can customize the threshold that triggers one diagnosis event and the severity of the network issue.

(Figure 4 Customize Threshold)
Conclusion
It is always good to maintain the network running smoothly and properly without any problems. However, if a network issue arises, we must make sure it is quickly detected and solved before it affects the entire infrastructure and brings loss to our business. For the complexity of the network and variety of network applications, network troubleshooting is becoming more challenging and demanding. To have a powerful tool like Capsa in hand is must in everyday’s network management.
About Capsa
Capsa is packet sniffer software designed for network monitoring and troubleshooting purposes. It performs real-time packet capturing, 24/7 network monitoring, advanced protocol analyzing, in-depth packet decoding, and automatic expert diagnosing. By giving users insights into all of the network's operations, Capsa makes it easy to isolate and solve network problems, identify network bottleneck and bandwidth use, and detect network vulnerabilities, external attacks and insecure applications.
About Colasoft
Ever since 2001, Colasoft has been dedicated in providing all-in-one and easy-to-use network analysis software for customers to monitor, analyze, and troubleshoot their network. Up to now, more than 4000 customers in over 70 countries trust the flagship product – Capsa as their network monitoring and troubleshooting solution. The company also offers four free network utilities: Colasoft Packet Builder, Colasoft Packet Player, Colasoft MAC Scanner, and Colasoft Ping Tool. Learn more today at http://www.colasoft.com/